Tesla Door Phone Decoded (Not That Tesla) [Hackaday]
[Danman] has digital door phones manufactured by Tesla — or at least, a Tesla, as they’re not to be confused with the carmaker, though. The problem is if someone comes to the door when no one’s home, there’s no remote indicator. The answer? Reverse engineer the protocol and fix it.
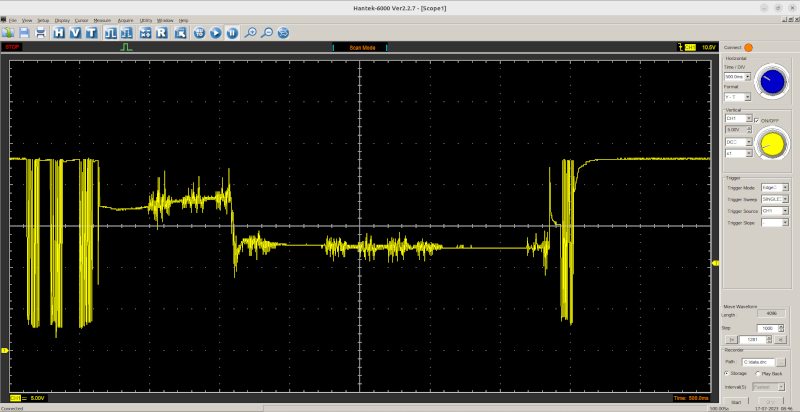
A quick dump on a storage scope showed the data clearly, but it wasn’t obvious what protocol it was using. After a little analysis, it proved the datastream used 4 PWM pulses as symbols with three symbols: one, zero, and stuffing sequence.
Once you can read the bits, it is easy to determine that each frame consists of a 16-bit destination and source address, along with a command byte and a checksum byte. Each station can have an ID from 000 to 999 although you can only dial up to number 323. Some nodes are special, and there are ways to address particular units.
Connecting to the hardware took a transformer for isolation. Honestly, unless you have this exact hardware, this isn’t likely to be something you can directly use. However, it is a great example of how you can figure out a specialized device and bend it to your will.
We love reverse engineering projects. In some cases, it is easier if you have a CT scan.

![tesla-door-phone-decoded-(not-that-tesla)-[hackaday]](https://i0.wp.com/upmytech.com/wp-content/uploads/2023/07/133557-tesla-door-phone-decoded-not-that-tesla-hackaday.png?resize=800%2C412&ssl=1)